»
Stiri
»
How to create strong, secure passwords by learning how to crack them
»
Stiri
»
How to create strong, secure passwords by learning how to crack them
|
« Inapoi la pagina anterioara |
How to create strong, secure passwords by learning how to crack them

Create stronger, more secure passwords: We are nagged to do it all the time, but few of us actually make the effort. Meanwhile, passwords continue to be stolen, leaked, and cracked on a regular basis. So this time we’re hoping to get your attention by looking at it from the attacker’s side! We'll show you how passwords are cracked and even how to do it yourself, so you can see exactly why a strong password matters.
As our brief foray with a cracking tool will show you, your only protection against a determined password-cracker is—you guessed it—a long, complex string of 10 or more characters. Anything shorter, let alone simpler, is too easy to crack. Know that, and suddenly using a password manager looks a lot easier than trying to create passwords all by yourself. We also have tips on how to pick a very strong password, too!
Read on to learn more about how passwords are hidden from crackers, and how crackers try to tease them out.
Note: We tried cracking tools on our own passwords for this story. Using cracking tools to break into a website, service, or file that’s not yours is at best, unethical—and at worst, illegal. Take our advice and don’t even think about it.
How hashing protects your password
To deter crackers, a responsible website won’t store a password in its original form, in what’s known as plaintext. Instead, it will use what’s known as a hashing algorithm—common ones include MD5, SHA2, or SHA3, but there are many more—to take your password and turn it into a “hash,” a string of seemingly random numbers and letters.
The site won’t advertise which hashing algorithm it uses, as that would only make life easier for crackers. It might even take that first hash and hash it again, or add what’s known as a “salt”—a series of additional characters that makes your password even harder to tease out.
Creating an example hash is easy. For an MD5 hash, all you need to do is visit a site like MD5hashgenerator.com and hash an example word. (We would recommend not hashing a password you actually plan to use, for security’s sake.) MD5 is an older algorithm that's considered unsafe for a number of reasons, but it's still useful for demonstrating how password hashing and cracking work.
Thus, the password maverick becomes 55f9c405bd87ba23896f34011ffce8da.
As a further safeguard, the hashing algorithms work in only one direction. By design, you can’t un-hash a hashed password. Furthermore, with a one-way hash, the website or service doesn’t even need to know your password. The site just needs to hash your password and compare it to the hash stored on file. If the two match, you’re in. That's also how we begin to crack passwords.
How hashed passwords can still be cracked
Hashing is an important and fundamental step in protecting your password, but it doesn’t make your password impervious. All a password cracker has to do is replicate the process: Guess a password, hash it, and then compare it to the leaked password hash. If a cracker guesses right, they’ve unfortunately learned your password. If they’re wrong, they try again...over and over and over.
You simply can’t try to log in to Amazon, however, pretend you’re Bill Gates, and guess and guess and guess passwords until you get lucky. Ditto for a bank. A smartly designed website will have some form of control built in. Guess wrong too many times, and the site will probably flag the account or your IP address as a potential hacker, and either limit or block your login attempts entirely.
After a password breach, however, all bets are off. Take this example: In 2019, a massive trove of 2.19 billion email addresses/usernames and passwords leaked to the web, part of the Collections breach. Once those hashed passwords were published, there wasn't any way of stopping those with access to them from downloading them to their own PC, then trying to crack them without any of the rate controls enforced by a live website.
In this scenario, all the cracker really needs to know—or to guess—is the algorithm used to hash the passwords, then apply the PC’s enormous computing power to make billions of guesses per second to crack a password. Your hashed password’s enemies are time, computing power, and smart guesses. (Here’s how to tell if your password has been stolen.)
How hard is it to crack a password?
Cracking a password can get enormously complex, very quickly. A single-character password already represents 26 possibilities—or 52, when you add upper-case letters. Adding the numerals 0-9 brings you to 62 possibilities, and special characters lift the total to 96. (Foreign-language keyboards can affect this, and some sites might require only a subset of the available special characters.) Based on a list of 96 characters, even a four-character password like t7G( would theoretically require up to 84,934,656 (96 to the 4th power) separate guesses.
So does that mean a four-character password is safe? Absolutely not.
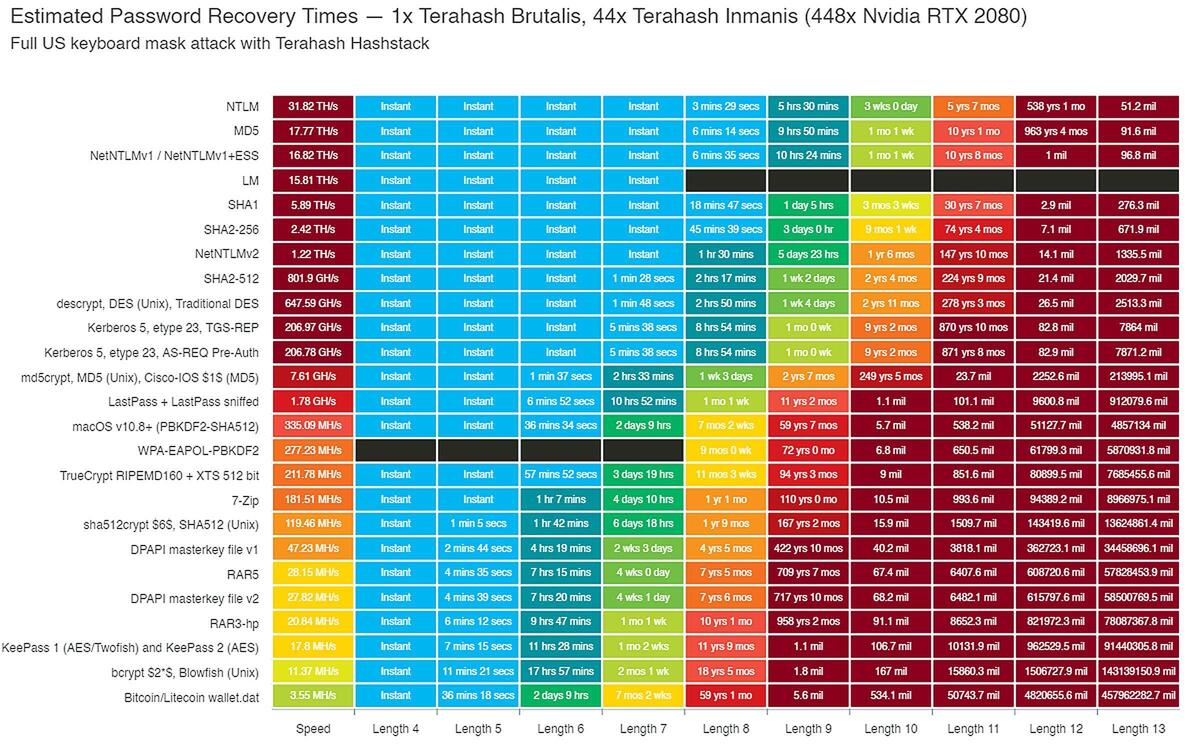
The graphic shown below, put together in 2018 by professional password-cracking company Terahash, shows both how impossibly easy—and how incredibly difficult—password-cracking can be. The chart lists major hashing algorithms on the left. The color immediately adjacent indicates how quickly a password hashed in each algorithm can be cracked by Terahash’s password-cracking technology. The topmost algorithm, NTLM, proved the fastest to crack overall, along with many other algorithms coded dark red; while the Bitcoin/Litecoin algorithm at bottom took the longest, and is coded yellow-green.
But the algorithm is only part of the challenge. The other is the length of the original password. The other columns’ color-coding represents the ease with which a hashed password in each algorithm can be cracked, based upon its original length. That sea of turquoise blue represents shorter passwords of four to eight characters, which can be cracked “Instantly” or in up to an hour, depending on the hash algorithm used. The dark-green areas represent passwords that can take up to a day to be cracked, while bright-green ones take up to a week, and so on. Gradations of orange and red represent passwords that take a year or more to crack.
There are two important takeaways from this chart. First, shorter passwords of four to six characters were easy for Terahash to crack regardless of the algorithm. Second, a random password’s resistance to being cracked was massively increased simply by making it at least 10 characters long.
Cracking passwords follows the same progression as cryptocurrency mining: CPUs are somewhat efficient, GPUs are much more efficient, and only well-funded researchers or nation-states have tried to develop dedicated password-cracking ASICs. Terahash’s technology uses a cluster of powerful GPUs, so its technology is going to be much more powerful than what your PC can bring to bear. Still, all you really need to crack passwords is a PC with a dedicated GPU. We used a Microsoft Surface Book 3 with a GeForce GTX 1660 Ti GPU as a testbed, hitting a peak of guessing 6,959 megahashes—almost 7 billion hashes—per second. Desktop PCs can process even more.
How to crack passwords with Hashcat
There are many software tools available to crack passwords, though we’re going to focus on just one. Hashcat attacks password hashes through a combination of brute force, rules, masks, and dictionary attacks, all of which we’ll explain later.
Originally, Hashcat demanded specialized Linux distributions like Kali Linux, which were designed for penetration testing. You can download Kali Linux via the Microsoft Store app and put it within a Windows Subsystem for Linux shell. (Just make sure it’s Windows Subsystem for Linux 2, which allows your GPU to perform computations.) There’s an easier way, though: hashcat has a Windows binary, which means you can download it for Windows. It runs using the Windows command-line interface, tapping either Nvidia's CUDA API or a more generic OpenCL driver.
There are three main components to Hashcat: the program itself, and two text files you’ll need to create. One file contains the hashes to be cracked, and the other is a repository for the cracked hashes. In this case, I called them “hash.txt” and “cracked.txt”. I created a simple hash of an easy-to-guess password, copied the password hash into the hash.txt file, saved it, and closed the text editor. Then I opened the Windows Command Line app with administrative privileges to run Hashcat, navigating to the directory in which Hashcat is stored.
We’re going to start by using Hashcat to “brute-force” crack passwords—guessing endless series of possible passwords in hopes of hitting upon the right one. You can read the documentation if you’d like at the Hashcat FAQ, but typing this into the Command Line app will get things started:
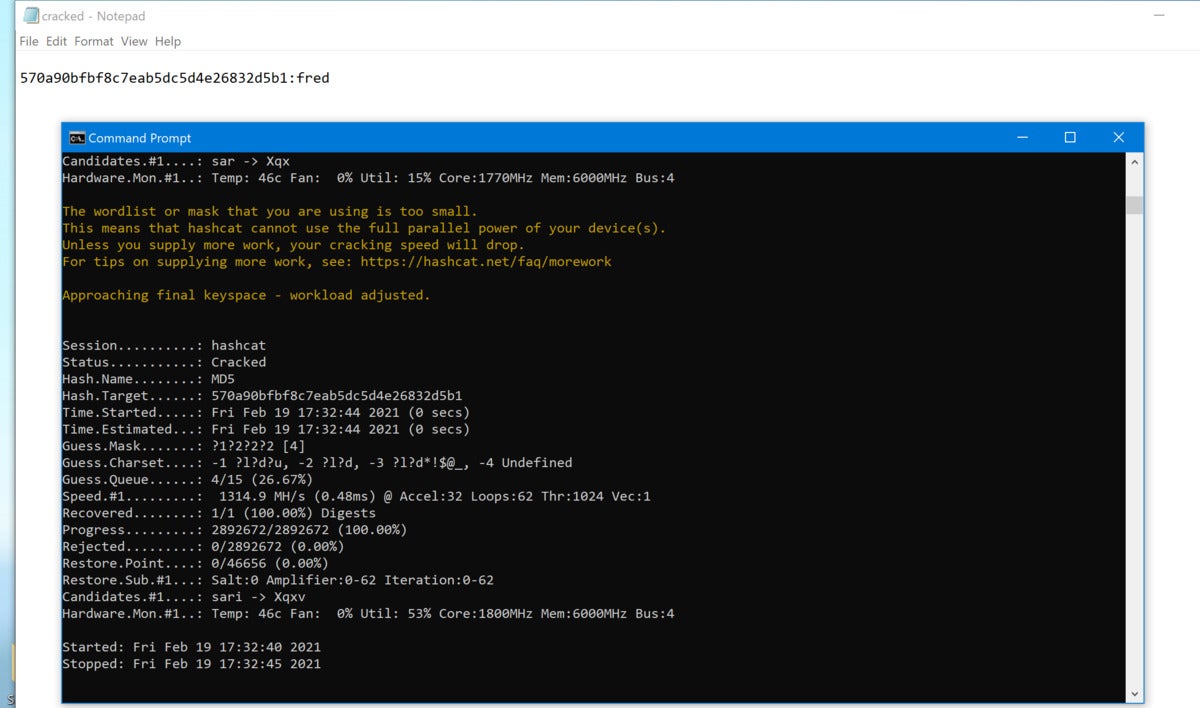
hashcat -m0 -a3 -o cracked.txt hash.txt
A short, simple password like fred should take just moments to crack, and it does.
To double-check the hashed password, you can open the file in which the cracked passwords are stored. You’ll see the hash, followed by the plaintext, cracked password.
I made quick work of simple four-character hashed passwords, such as 4289, yniu, tg5f, and Trxc. Note that while the latter combinations added a bit of complexity, they all were cracked in four seconds or less. But then I tried jRtw, and something very interesting happened: using the default settings, Hashcat couldn’t crack my hash within seconds. Or minutes. Or more than an hour.
Why? My guess is that I broke a mask. And that’s a good thing.
Rules, masks, and dictionary attacks
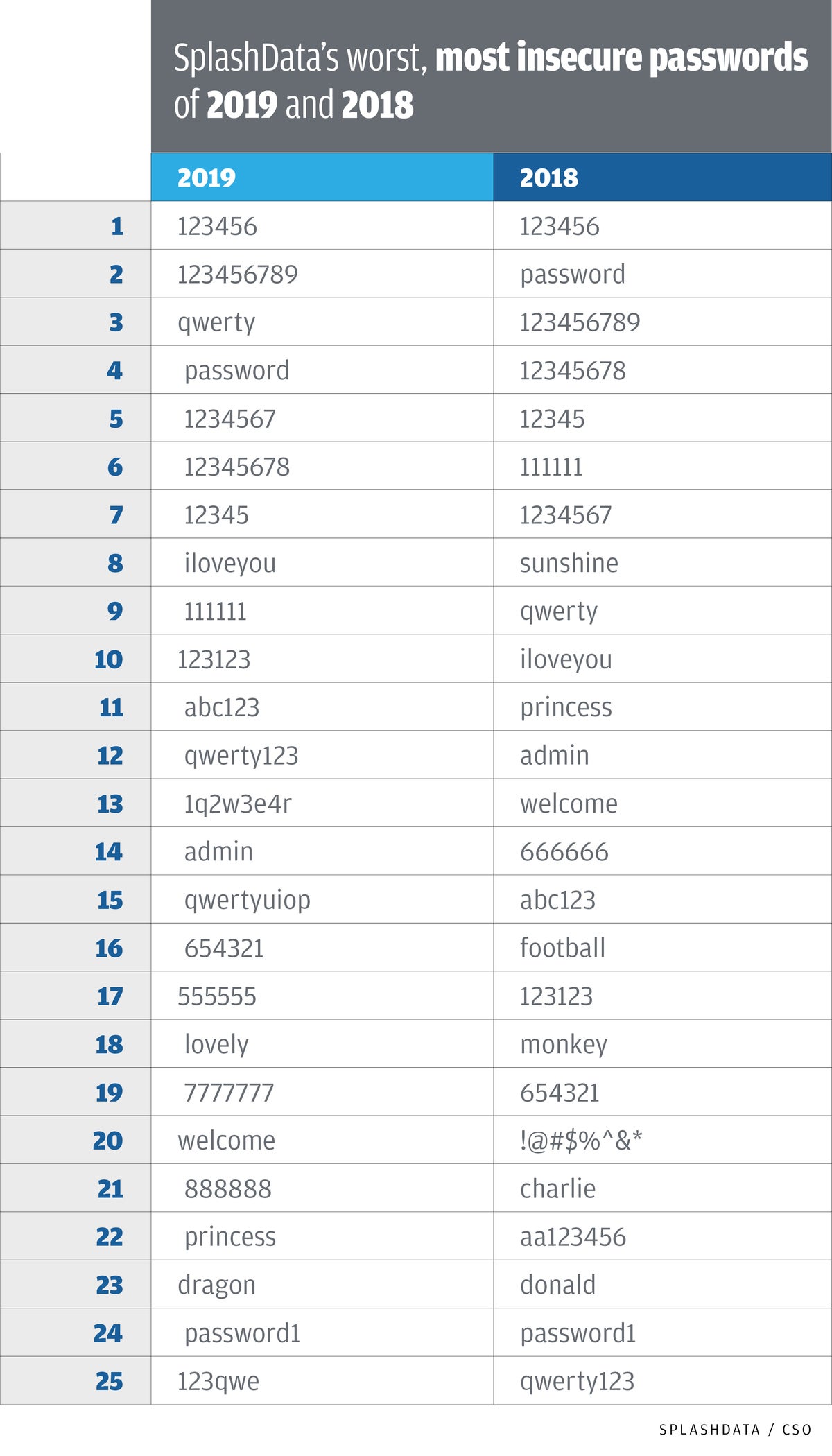
Password crackers know as well as we do that longer and more complex passwords are harder to crack. But they also know that humans cheat, using words and patterns to create passwords, rather than long and random strings. That means password crackers can cheat, too, using tactics known as “rules” and “masks,” combined with “dictionaries” of common passwords. For instance, SplashData’s chart of the most insecure passwords of 2018 and 2019, below, should be part of any respectable cracker’s dictionary attack. It also points out the danger of reusing passwords, because once a cracker finds it out they will try it on other accounts of yours, just in case you got lazy.
A dictionary attack may use single words or strings of words, combined with a list of common first names, plus the most common passwords. In 2009, for example, an app vendor called RockYou was breached, and the database of unencrypted passwords, reportedly 30 million strong, was leaked to the web. This database forms one of the most common dictionary attacks available today.
A mask is a separate approach, using patterns to simplify the process. Ever start your password with a capital letter, and end with a punctuation mark? What about ending your password with two numerical digits? These are both examples of masks, and they can and are programmed into a password cracker to reduce the number of potential hashes.
A rule is a more complex expression, often combining a mask and a dictionary attack. If your password combines a common word with two digits, or combines the first name of your aunt with a number and an exclamation point at the end, a rule can help crack that password much more quickly than trying random guesses. That’s one advantage of using a password manager—not only will it generate a long password, but that password will be much more random than one you yourself would typically generate.
Remember, though—and this is important!—a cracking tool has absolutely no idea if your password is four characters long, or fourteen. In the example of the unexpectedly difficult four-character password I generated, what apparently happened is that Hashcat’s default mask attack figured that it was most efficient to simply skip anything that wasn’t preprogrammed into its mask files and move on from trying to crack four-character passwords to five-character passwords.
Does that mean that jRtw is an uncrackable password? Of course not! In this case, another cracker could simply write a rule that tells Hashcat to try every four-character password before moving on. It does mean, however, that a well-designed password may be able to evade detection.
What you should learn from this
If nothing else, you should take away three lessons from all this:
- The longer the password, the better. Based on the Terahash example above, a 10-character or longer password appears safe, for now.
- The more complex the password, the better. Random passwords are the strongest option, but at the least, ensure that you have at least one lower-case character, an upper-case character, a number, and a special character like an &, #, or ]. The more, the better.
- Password managers are probably the best solution for password management.
It bears repeating: A password manager—we’ve reviewed the best paid password managers, and we’ve also looked at the best free password managers—is the strongest and the most convenient solution. Why wrestle with coming up with a list of long, complex passwords if a service will do it for you?
That’s what makes password cracking so fascinating. It’s both trivially easy to crack a password—and next to impossible. The difference between the two depends on the choices you make.